Tuesday, September 26, 2017
Download Amlogic Tools BootCardMaker USB Burning Tool v2 0 0 140306 Alpha
Download Amlogic Tools BootCardMaker USB Burning Tool v2 0 0 140306 Alpha



download file now
Tablet imei repair tools Free Download Here
Tablet imei repair tools Free Download Here
supported allwinner A20 cpu
supported allwinner a10 cpu
supported allwinner a13 cpu
supported Mtk 6572,65xx cpu
suppotred allwinner 2g modem imei writing
supported allwinner 3g modem imei writing
Different imei writing tools for different modem version
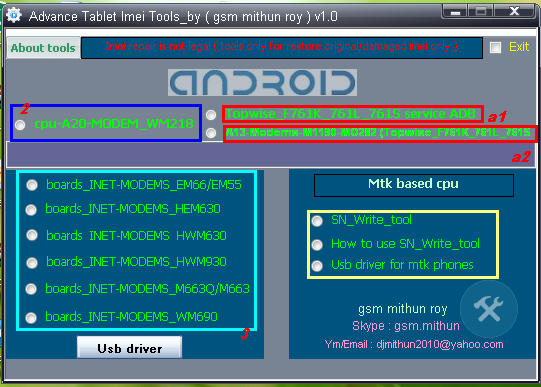
note : All tools need usb debugging on
For any tablet imei repair
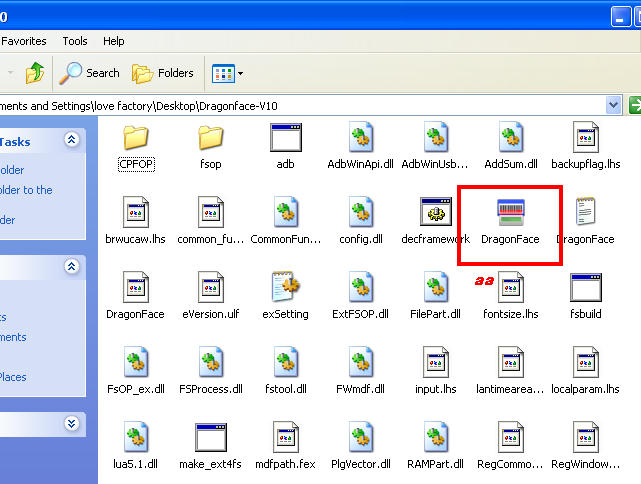
A1 & a2 : Click a1 topwise_F761k_761l_761s service Adb copy or extract Dragonface_v10 folder to desktop > open folder and deagonface.exe,now close advance tablet imei tools and open tool aagin now click a2 a13 modems1190-m0228 (topwise_F761k_761l_761s) then connect tablet and repair
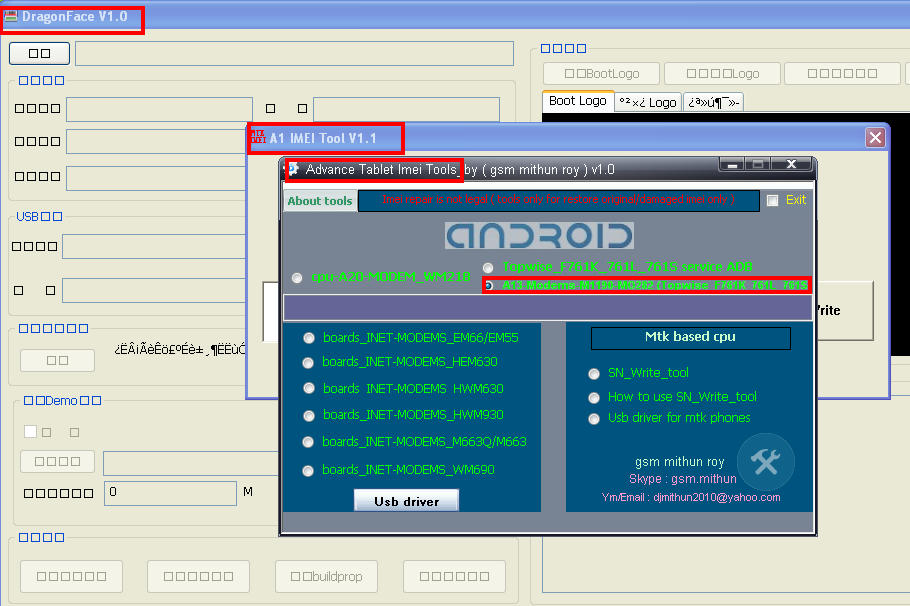
2 : just click and fill the box imei digit press write
3 : click to any tools
according matches su al modem device enter 15 digit imei in cmd tool press enter then restart device and check
download file now
Universal android Letest tools Free Activate Here
Universal android Letest tools Free Activate Here
Download Software for Free
:: How to Active Free Tutorial ::
..:: ScreenShot 1 ::..
..:: ScreenShot 2 ::..
download file now
Sunday, September 24, 2017
Flash Tutorial SP Flash Tools SPD upgrade tools and Free Download !!
Flash Tutorial SP Flash Tools SPD upgrade tools and Free Download !!
Install ROM:

2). Remove the battery and insert it again
3). Connect your phone to a computer cable. The operating system detects a new device
4). Disconnect the cable from the computer.
5). Run SPMultiPortFlashDownloadProject.exe
6). Choose File> Open File Agent download and specify the file MTK_AllInOneDA.bin (it is in the folder SP_MDT).
7). Click Scatter File and select the _Android_scatter.txt file (its in the folder with the rom).
8). Click "Start all".
9). Connect your phone to a computer cable. The program should see and blink. If the phone is not detected, then unplug it from the computer,
remove and insert the battery (if the battery is removable) and reconnect it to the computer.
10). After (OK) click Stop and disable any phone.
11). Completed.
________________________
Download Link:
FactoryDownload/UpgradeDownload/ResearchDownload

2 Run UpgradeDownload or FactoryDownload or ResearchDownload, connect your android device to the computer
3 Click on "Load packet"and add the .pac
4 Click on "Start"
5 During the flashing your mobile will restart automatically
6 Finish
Download Link:
SPD Upgrade Tool (Flash Tool) Download

download file now
Saturday, September 23, 2017
Download MTK Droid Root Tools v2 5 3
Download MTK Droid Root Tools v2 5 3

Download MTK Droid Root & Tools v2.5.3 from here, here or here.
You can also download MTK Droid Root & Tools v2.4.6 & v2.5.2 from here.
- adb drivers are installed, in a device manager there shouldnt be unknown devices at connection of switched-on phone. ADB Drivers here.
- USB debugging in Developer options of System setting is allowed.
1. Make scatter by means of MTKDroidTools
Scatter is the text file with addresses of the blocks, necessary for the SP FlashTool program. After creation of scatter dont close the main window of the program! Otherwise once again it is necessary to turn on phone.
2. In SP FlashTool choose this scatter and go on the Read Back tab.
3. Choose path and a ROM file name. Click on Add button. Double click of a mouse on the appeared line. Choose a file name, the name has to begin with ROM_ as offers FlashTool! Remember path and the name of ROM_ file.
4. Determine the ROM_ size. Type has to stand in HEX. In the field of Start Address it is necessary to write down 0x000000. In the field of Length we copy from scatter the address of the block following after RECOVERY or the address of other block for fuller backup. For phones with type of the blocks EXT4 it is the cache block address. The number in the Hex format has to begin with 0x
5 . Choose Read Page Only on yaffs2 type blocks phones. In FlashTool choose Read Page Only in the field of Read Method. If this field isnt present, the window with this question can emerge, too we choose Page Only. On phones with EXT4 blocks it doesnt get out (as a rule).
6. Read Back ROM_.Click on Read Back button and connect the switched-off phone to PC. Here the options depending on a concrete phone are possible. Maybe it is necessary to press at the same time with connect of a cable the camera or volume buttons. Experiment and study work with FlashTool in threads with similar phones! On some MT6573 models, for example on B63, it cant be executed with any combinations and only testpoint need!
7. Prepare files for FlashTool and make CWM. If everything passed without errorss, we open the MTK Droid Root & Tools window which we left on 1th step. If for some reason the window isnt present, it is necessary to turn on phone and to connect it to the program. Click on To process file ROM_ from FlashTool button and choose the ROM_* file saved on the 6th step. At successful unpacking rom it will be offered to choose CWM from similar phone. Chosen CWM it is checked on compliance to the connected phone and if ok, the CWM is created. Starting with v2.4.0 CWM it is made automatically and the file from similar phone shouldnt be looked for any more!
?ttention! Yaffs2 type blocks from this backup cant be Downloaded to phone, they arent correct! Use backup on 9th step if phone have yaffs2 type blocks!
9. Make backup, install SuperUser etc. Load phone in CWM mode, connect to MTK Droid Root & Tools, go on the tab root, backup, recovery and, pressing on this tab the necessary buttons, we do:
- backup! (if in phone there is yaffs2 type blocks, do here surely, they received with readBack on 7th step arent correct)
- install superuser (often mean "get root" under it)
- and other if need
Never needlessly Download preloader and DSP_BL blocks! It is always dangerous! On some models of phones (for example Alcatel) you will have a brick even if you download these blocks read from phone which you own! Always remove from them marks in SPFT!
download file now
Wednesday, September 20, 2017
Tablet TOOLS FIX screen shift FIX inverted axes on TS Free DOWNLOAD
Tablet TOOLS FIX screen shift FIX inverted axes on TS Free DOWNLOAD
DOWNLOAD TOOLS
script-bin - Download - 4shared - Toxic RR
or
script-bin
HOW TO USE
First of all extract the folder script-bin from archive you just downloaded to C:
Now go to C:script-bin directory and from there execute the wanted tools
Your tablet need to be rooted and adb enabled in order to use this fixes.
FIX SCREEN SHIFT
execute screenshift.cmd from C:script-bin directory and follow the numbers
1. Pull script.bin from tablet
2. Transform script.bin to script.fex
3. Change lcd parameters to resolve screen shift
4. Transform script.fex to script.bin
5. Push scrip.bin to tablet
6. Reboot tablet
- on step 3 you will see current settings and most of the first 4 choice will fix your display, if not try the rest
FIX INVERTED AXES
execute changexy.cmd from C:script-bin directory and follow the numbers
1. Pull script.bin from tablet
2. Transform script.bin to script.fex
3. Revert X axe
4. Revert Y axe
5. Revert X_Y axe
6. Transform script.fex to script.bin
7. Push scrip.bin to tablet
8. Reboot tablet
- on steps 3, 4 and 5 you will see the current settings and you need to choose to reverse
TIPS
if you want to fix faster just copy your original script.bin to C:script-bin and by executing one of the program you can find actual settings then after you know your setting just reuse program from first step
- you have x,y,xy try all combination: 0,0,0 - 0,0,1 - 0,1,0 - 0,1,1 - 1,0,0 - 1,0,1 - 1,1,0 - 1,1,1
you can solve your tablet display issue FIX on THIS Tool
download file now
Monday, September 18, 2017
Download ACTIONS Pad Tools Pack
Download ACTIONS Pad Tools Pack

Download ACTIONS Pad Tools Pack from here, here or here.
ACTIONS Pad Tools Pack content:
- ACTIONS Pad Firmware Modify Tool_V1.08
- ACTIONS Pad Image Maker Tool_V1.02
- ACTIONS Pad Product Tool_V1.07.02
download file now
Friday, September 15, 2017
Download Acer Iconia A500 Tools by blackthund3r
Download Acer Iconia A500 Tools by blackthund3r
Download Acer Iconia A500 Tools by blackthund3r from here or from here.
The pack contains:
- A500 Manager v.1.1.1 by blackthund3r
- ICS Root 7.2.0 for Iconia Tab by blackthund3r
- blackthund3r_A500_APX_Flash_Tool_v0.4.1
- blackthund3r_APX_Flash_Bundle_Builder_V0.2.1
You can download Acer Iconia USB Driver from here or from here.
You can download more stuff for Acer Iconia A500 from here.

download file now
Wednesday, September 13, 2017
Tools for Internet anonymity
Tools for Internet anonymity
The Onion Router, aka Tor (Figure 1) is free software which aims to allow its users to be untraceable on the internet. It attempts to do so by connecting their devices to the Tor network before forwarding their request to the actual destination. The Tor network is a volunteer network, consisting of several relays used to conceal a users location. Data packets in the Tor network dont use a direct path from source to destination; instead they use a randomly chosen pathway. To create a pathway, a circuit of encrypted connections through relays is build. Each relay decrypts a layer of encryption. That way every relay knows only from which relay it got data from and which relay its giving the data to. The final relay decrypts the innermost layer of encryption and sends the original data to its destination without revealing the source. There are sites that cant be accessed via Google but can be reached with Tor, such as .onion sites. These sites are short-lived and one must be up to date to know which sites are still working. For that reason, there are several .onion directories which contain many links to active sites, such as ahmia.fi.
 |
| Figure 1. Tor logo |
 |
| Figure 2. I2P logo |
download file now
Monday, September 11, 2017
Download MTK Droid Root Tools v2 5 2
Download MTK Droid Root Tools v2 5 2

- adb drivers are installed, in a device manager there shouldnt be unknown devices at connection of switched-on phone. ADB Drivers here.
- USB debugging in Developer options of System setting is allowed.
1. Make scatter by means of MTKDroidTools
Scatter is the text file with addresses of the blocks, necessary for the SP FlashTool program. After creation of scatter dont close the main window of the program! Otherwise once again it is necessary to turn on phone.
2. In SP FlashTool choose this scatter and go on the Read Back tab.
3. Choose path and a ROM file name. Click on Add button. Double click of a mouse on the appeared line. Choose a file name, the name has to begin with ROM_ as offers FlashTool! Remember path and the name of ROM_ file.
4. Determine the ROM_ size. Type has to stand in HEX. In the field of Start Address it is necessary to write down 0x000000. In the field of Length we copy from scatter the address of the block following after RECOVERY or the address of other block for fuller backup. For phones with type of the blocks EXT4 it is the cache block address. The number in the Hex format has to begin with 0x
5 . Choose Read Page Only on yaffs2 type blocks phones. In FlashTool choose Read Page Only in the field of Read Method. If this field isnt present, the window with this question can emerge, too we choose Page Only. On phones with EXT4 blocks it doesnt get out (as a rule).
6. Read Back ROM_.Click on Read Back button and connect the switched-off phone to PC. Here the options depending on a concrete phone are possible. Maybe it is necessary to press at the same time with connect of a cable the camera or volume buttons. Experiment and study work with FlashTool in threads with similar phones! On some MT6573 models, for example on B63, it cant be executed with any combinations and only testpoint need!
7. Prepare files for FlashTool and make CWM. If everything passed without errorss, we open the MTK Droid Root & Tools window which we left on 1th step. If for some reason the window isnt present, it is necessary to turn on phone and to connect it to the program. Click on To process file ROM_ from FlashTool button and choose the ROM_* file saved on the 6th step. At successful unpacking rom it will be offered to choose CWM from similar phone. Chosen CWM it is checked on compliance to the connected phone and if ok, the CWM is created. Starting with v2.4.0 CWM it is made automatically and the file from similar phone shouldnt be looked for any more!
?ttention! Yaffs2 type blocks from this backup cant be Downloaded to phone, they arent correct! Use backup on 9th step if phone have yaffs2 type blocks!
9. Make backup, install SuperUser etc. Load phone in CWM mode, connect to MTK Droid Root & Tools, go on the tab root, backup, recovery and, pressing on this tab the necessary buttons, we do:
- backup! (if in phone there is yaffs2 type blocks, do here surely, they received with readBack on 7th step arent correct)
- install superuser (often mean "get root" under it)
- and other if need
Never needlessly Download preloader and DSP_BL blocks! It is always dangerous! On some models of phones (for example Alcatel) you will have a brick even if you download these blocks read from phone which you own! Always remove from them marks in SPFT!
download file now
Sunday, September 10, 2017
Easy Team Tools V2 2 Download
Easy Team Tools V2 2 Download

This easy process is applied at that time when your phone is going slow or hanged. After applying this tool your phone worked better then before. This updated downloading link allows you to free and fast downloading, which is cleaned of dangerous viruses.
You know that its process is not difficult but if you have not done before it then be carefully during all this process, because a little mistake can make a big issue for you.

download file now
Saturday, September 9, 2017
Download RK3xxx firmware tools by Sergio Poverony
Download RK3xxx firmware tools by Sergio Poverony

Download RK3xxx firmware tools pack from here, here or here.
RK3xxx firmware tools pack content:
- DriverInstaller_2014
- RK3xxx_firmware_tools_3.8.75.2
- RK3xxx_firmware_tools_4.0.02.00
- RK3xxx_firmware_tools_4.0.12.00
- RK3xxx_firmware_tools_4.0.33.00
- RK3xxx_firmware_tools_4.1.17.00
- RK3xxx_firmware_tools_4.1.22.00
- RK3xxx_firmware_tools_4.2.22.00
download file now
Thursday, September 7, 2017
Top 10 Best Hacking Tools For Learners
Top 10 Best Hacking Tools For Learners
1. Nmap

In hacking, Nmap is usually used in the footprinting phase to scan the ports of the remote computer to find out wich ports are open.
2. Wireshark

3. Cain and Abel

Cain and Abel is a multipurpose windows only hacking tool. It is a bit old now, but it still does the job well. Cain can be used to crack windows password, perform man in the middle attacks, capture network passwords etc.
4. Metasploit

Metasploit is a huge database of exploits. There are thousands of exploit codes, payloads that can be used to attack web servers or any computer for that matter. This is the ultimate hacking tool that will allow you to actually "hack" a computer. You will be able to get root access to the remote computer and plant backdoors or do any other stuff. It is best to use metasploit under linux.
5. Burp Suite

Burpsuite is a web proxy tool that can be used to test web application security. It can brute force any login form in a browser. You can edit or modify GET and POST data before sending it to the server. It can also be used to automatically detect SQL injection vulnerabilities. It is a good tool to use both under Windows and Linux environments.
6. Aircrack-ng

Aircrack-ng is a set of tools that are used to crack wifi passwords. Using a combination of the tools in aircrack, you can easily crack WEP passwords. WPA passwords can be cracked using dictionary or brute force. Although aircrack-ng is available for Windows, it is best to use it under Linux environment. There are many issues if you use it under Windows environment.
8. Nessus

Nessus is a comprehensive automatic vulnerability scanner. You have to give it an IP address as input and it will scan that IP address to find out the vulnerabilities in that system. Once you know the vulnerabllities, you can use metasploit to exploit the vulnerablity. Nessus works both in Windows and Linux.
10. THC Hydra

Hydra is a fast password cracker tool. It cracks passwords of remote systems through the network. It can crack passwords of many protocols including ftp,http, smtp etc. You have the option to supply a dictionary file which contains possible passwords. It is best to use hydra under linux environment.
9. Netcat

Netcat is a great networking utility which reads and writes data across network connections, using the TCP/IP protocol. It is also known as the swiss army knife for TCP/IP. This is because netcat is extremely versatile and can perform almost anything related to TCP/IP. In a hacking scenario, it can be used as a backdoor to access hacked computers remotely. The use of netcat is limited only by the users imagination. Find out more about netcat at the official website.
10. Putty

Although putty is not a hacking software by itself, it is a very useful tool for a hacker. It is a client for SSH and telnet, which can be used to connect to remote computers. You may use putty when you want to connect to your Backtrack machine from your Windows PC. It can also be used to perform SSH tunneling to bypass firewalls.
Note: This list is not comprehensive. There are many tools that I have left out. Those tools that did not make the list are; Sqlmap, Havij, Acunetix Web Scanner, SuperScan, John the Ripper, Kismet, Hping3.
Have you always wanted to know how to become a hacker? Great! Read this article and learn how to become a hacker.
download file now
Wednesday, September 6, 2017
Download SPD Upgrade tools semua versi
Download SPD Upgrade tools semua versi

Smartphone Android yang mengalami bootloop atau Mati total, Masih dapat diatasi dengan melakukan flash ulang asalkan Smarphone Android masih terdeteksi PC, Jika kerusakan pada software, Setelah melakukan Flash, Smartphone Android akan kembali normal .
untuk fiturnya silahkan coba sendiri sama anda sob,
download file now
Sunday, September 3, 2017
Tablet tools LiveSuitPack v1 07 1 09 including USB drivers DOWNLOAD
Tablet tools LiveSuitPack v1 07 1 09 including USB drivers DOWNLOAD
download file now
Saturday, September 2, 2017
Download Acer A500 Tools Pack v1 0
Download Acer A500 Tools Pack v1 0

Download Acer Iconia Tab A500 Tools Pack v1.0 from here, here or here.
Download Acer A500 Tools Pack v1.0 contains:
- A500 UUID Read Tool
- A500 SN Update Tool
- A500 Diagnostic Tool
- A500 UUID weekly update_WWxx
- Acer A500 service tools official release and introduction.pdf
- A500 Service Tool Introduction_v1.0.pdf
- A500 OS_SD Upgrade SOP_v1.0.pdf
- A500 UUID Read Tool and Maintenance SOP_v1.0.pdf
- A500 Serial Number update tool SOP_v1.0.pdf
- A500 Diagnostic tool SOP_v1.1.pdf
- A500 Diagnostic tool SOP_v1.0
- A500 Diagnostic Tool
- Acer ICONIA tab A500 Diagnostic tool official release.pdf
- sg_iconia_tab_a500_20110421.zip
- A500 OS_SD Upgrade SOP_v1.0.pdf
- SG_ICONIA Tab A500_20110421.pdf
Enjoy this pack, share is love!
download file now
Tools for Android malware analysis
Tools for Android malware analysis
This post gives some tools for which I managed to find some info and think that can be useful for dynamic and static malware analysis.
When doing malware analysis, it is necessary to prepare safe and reliable environment for running the malware in order to observe its behavior or perform procedures of reverse engineering. Android malware, as much as other platforms, demands such environments which is bit hard to find. One reason is because malware analysis task demands high processor performance and memory capacity. Also, emulators provided by official Android SDK are very slow and we don�t want to run malware on real Android device. This makes dynamical malware analysis very annoying and tedious. Some tools like CopperDroid address this problem very nicely. Specifically CopperDroid provides web interface where you can upload apk file which is then analyzed and results of dynamic analysis are given. Downside of this approach is that it maybe won�t find all threats.
Following list enumerates some tools for Android malware reverse engineering, debugging, monitoring and emulating behavior of an Android device:
- Androguard � Tool written in Python which can be used to analyze android application. Some of the features are: disassembly/decompilation/modification of DEX/ODEX/APK format, diffing of Android applications, measure the efficiency of obfuscators,checking if an Android application is present in a database (malwares), risk indicator of malicious application
- APKinspector � Also written in Python but provides a GUI to aide analysis of APKs and their DEX code. APKinspector can help to generate reports for permissions used by the application, search and filter strings, classes and methods and more. Some of the current models used by APKinspector are based on Androguard
- Droidbox � Sandbox for dynamic analysis of Android applications. This tool gives hashes for the analyzed package, incoming/outgoing network data, file read and write operations, started services and loaded classes through DexClassLoader, information leaks via the network (files, SMS), circumvented permissions, cryptographic operations performed using Android API, listing broadcast receivers, sent SMS and phone calls.
- CopperDroid � out-of-the-box dynamic behavioral analysis of Android malware. To this end, CopperDroid presents a unified analysis to characterize low-level OS-specific (e.g., writing to a file) and high-level Android-specific behaviors (e.g., sending an SMS, placing a phone call). Based on the observation that such behaviors are however achieved through the invocation of system calls, CopperDroids VMI-based dynamic system call-centric analysis is able to faithfully describe the behavior of Android malware whether it is initiated from Java, JNI or native code execution. In addition, CopperDroid features a stimulation technique to improve code coverage, aimed at triggering additional behaviors of interest. Our initial experiments show that a proper malware stimulation strategy (e.g., sending SMS, placing calls) successfully discloses additional behaviors on a non-negligible portion of the analyzed malware.
- Android-apktool � Tool for reverse engineering Android APK format using Java runtime environment.
- Smali - assembler/disassembler for the DEX format used by Dalvik, Androids Java Virtual Machine implementation. Supports the full functionality of the DEX format, e.g. annotations, debug info, line info.
- Android-x86 - provides a ready-to-use virtual machine disk which can be simply mounted and used to run original Android on VirtualBox. The advantage of this method is that the experience is 99% like an actual Android device, but with higher processor performance, physical memory and storage.
download file now
Universal Android Tools v 6 0
Universal Android Tools v 6 0
Support:
ADB MODE
Wipedata
Reset pin/passworte
Reset face/gesture lock
bypass pattern
Reset user lock
Reset gmail ID
Wipe dalvik-cache
Read gmail ID
FASTBOOT MODE
Read device info
Wipe system
Wipe chache
Wipe recovery
Wipe boot image
Lock bootloader
Wipe data/format
Wipe user data
Wipe android secure
Fix low battery error
Unlock Bootloader
Other
Read gmail id
StartADB
Kill ADB
Key tool
Open music player
Music control
ROOT
UNROOT
VROOT
ROOT CHECKER
Batrey status
Read info
DOWNLOAD
download file now
